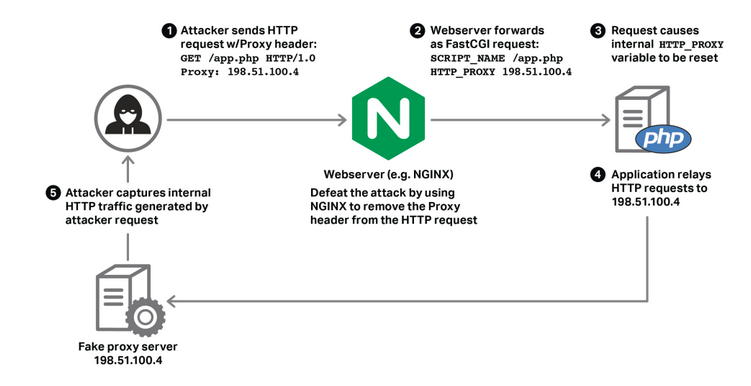
httpoxy is a set of vulnerabilities that affect application code running in CGI, or CGI-like environments. It comes down to a simple namespace conflict:
- RFC 3875 (CGI) puts the HTTP
Proxyheader from a request into the environment variables asHTTP_PROXY HTTP_PROXYis a popular environment variable used to configure an outgoing proxy
This leads to a remotely exploitable vulnerability. If you’re running PHP or CGI, you should block the Proxy header now. – httpoxy.org
httpoxy is a vulnerability for server-side web applications. If you’re not deploying code, you don’t need to worry. A number of CVEs have been assigned, covering specific languages and CGI implementations:
- Apache HTTP Server (CVE-2016-5387)
- Apache Tomcat (CVE-2016-5388)
- Go (CVE-2016-5386)
- PHP (CVE-2016-5385)
After receiving the updates from cyberstorm.mu, I immediately started some heavy research. For Nginx users, to defeat the attack, modifications can be carried out in the fastcgi_params file.
1. Create a file called test.php containing the following codes in the source code.
[root@server]# cat test.php
<?php echo getenv ('HTTP_PROXY') ?>
2. Launch a CURL as follows:
As you can see its “Affected”
[root@server]# curl -H 'Proxy: AFFECTED' http://127.0.0.1:/test.php AFFECTED
3. Add the following parameters in the /etc/nginx/fastcgi_params file
fastcgi_param HTTP_PROXY "";
4. Stop and start the Nginx Service
5. Conduct the test again. You should be vulnerable by now.
Several links available already explaining this vulnerability :
References:
- https://www.nginx.com/blog/mitigating-the-httpoxy-vulnerability-with-nginx/
- https://www.kb.cert.org/vuls/id/797896
- https://access.redhat.com/solutions/2442861
- https://httpoxy.org/#history
- http://www.theregister.co.uk/2016/07/18/httpoxy_hole/
- https://blogs.akamai.com/2016/07/akamai-mitigates-httpoxy-vulnerability.html
- http://www.zdnet.com/article/15-year-old-httpoxy-flaw-causes-developer-patch-scramble/
- https://access.redhat.com/solutions/2435541