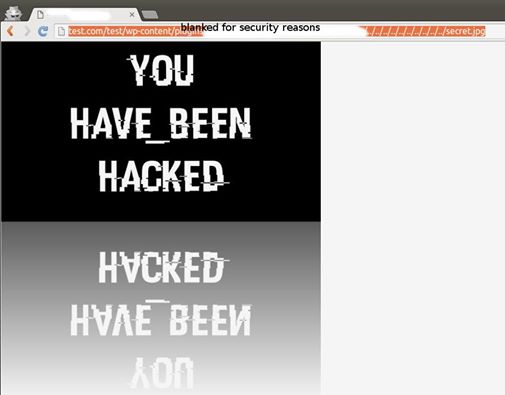
After having set up our network environment for the operation WTF, cyberstorm.mu team started working on several vulnerabilities around WordPress content management system. It started on Saturday the 14th of May where several proofs of concept (POC) were established. I was shocked to see how come it is easy to exploit a WordPress website. For security purpose, we have to blank parts of URLs before posting on social networks. No wonder, Loganaden Velvindron of cyberstorm.mu did not hesitate to give his opinion on Medium.com – “Many bloggers use it, because it is both easy to set up, and there is a rich ecosystem of WordPress plugins. WordPress has often been criticized due to its security record. What is more worrying is the varying quality of the WordPress plugins.”
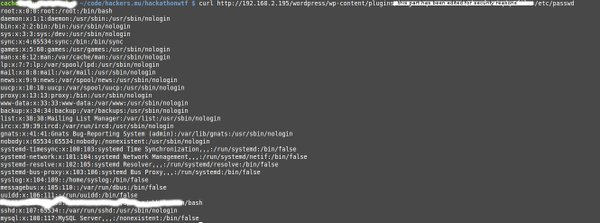
Operation WTF – WordPress Tiny flaws end up on Sunday the 15th of May 2016 after lines of codes were fixed up from many WordPress plugins. We can also notice how dangerous it is if a proper audit is not carried out on WordPress before putting a website to production. Here is another example where the /etc/passwd was retrieved by hackers Mauritius.
Patches were also written to fix up bugs. However, it is to be noted that for security reasons patches are not disclosed for the time being as at cyberstorm.mu we follow ethical rules and the aim to stay within the grey line is of paramount importance.