This is yet another successful hackathon carried out under the umbrella of cyberstorm.mu. Branded by the theme "Operation PB - Prison Break", members of cyberstorm.mu shows skills of security innovations. We have also Rahul who is our proud newest member has created Sandboxing on Strings
[google_ad data_ad_slot='' data_ad_format='rectangle'] [caption id="attachment_1305" align="alignnone" width="772"]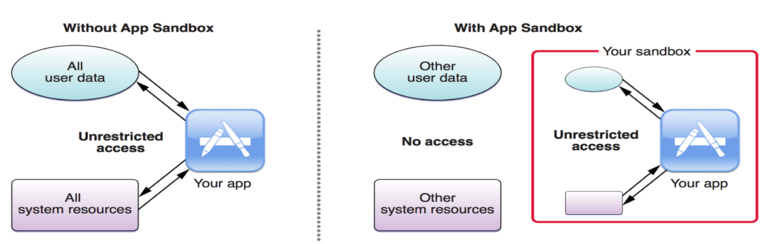
Our task was to find out vulnerabilities in a linux application and create a Firejail environment. Firejailing is the art of using a SUID program that reduces the risk of security breaches by restricting the running environment of untrusted applications using Linux namespaces and seccomp-bpf. It allows a process and all its descendants to have their own private view of the globally shared kernel resources, such as the network stack, process table, mount table. Firejail can sandbox any type of processes: servers, graphical applications, and even user login sessions. The software includes security profiles for a large number of Linux programs: Mozilla Firefox, Chromium, VLC, Transmission etc. To start the sandbox, prefix your command with “firejail”.
I decided to chose the CPIO, a tool to copy files to and from archives which recently was find to be vulnerable to DOS attack. Cvedetails.com explained the CVE-2016-2037 vulnerability where the cpio_safer_name_suffix function in util.c in cpio 2.11 allows remote attackers to cause a denial of service (out-of-bounds write) via a crafted cpio file. In brief, when a user is going to decompress a file, a user will be able to pass out file for the purpose of the attack. This has been achieved by QuickFuzz.
To sandbox the CPIO tools when decompressing files, Firejail application was used to isolate the program by making use of the syscalls. Here is the firejail environment :
You need to watch this video to understand firejail before reading the Profile :)
include /usr/local/etc/firejail/server.profile
include /usr/local/etc/firejail/disable-common.inc
include /usr/local/etc/firejail/disable-programs.inc
include /usr/local/etc/firejail/disable-passwdmgr.inc
caps.drop all
seccomp write,read,open,close,execve,access,brk,umask,munmap,fchmod,mprotect,mmap2,lstat64,fstat64,geteuid32,fchown32,set_thread_are,prctl,setresuid32,getgid32,setgroups32,setgid32,getuid32,setuid32,fcntl64,clone,rt_sigaction,nanosleep
Here are what participants in the hackathon are saying:
To prevent further vulnerabilities such as shown below from being used to target users, this firejail profile has been made. https://www.cvedetails.com/vulnerability-list/vendor_id-72/product_id-1670/GNU-Gzip.html - Yash
[google_ad data_ad_slot='' data_ad_format='rectangle']Decompressing .xz file within a sandboxing environment is just fascinating - Akhil
Many shell users, and certainly most of the people working in computer forensics or other fields of information security, have a habit of running /usr/bin/strings on binary files originating from the Internet. Their understanding is that the tool simply scans the file for runs of printable characters and dumps them to stdout - something that is very unlikely to put you at any risk. - Rahul
Previous hackathons carried out by cyberstorm Mauritius are as follows:
- Operation SAD
- Operation WTF
