Nmap is a free and open-source utility for network exploration and security auditing whilst ZeNmap is a multi-platform graphical Nmap frontend and results viewer. It was originally derived from Umit which was created as part of the Nmap/Google Summer of Code program. ZeNmap is compatible with almost all types of Operating systems. I have tested ZeNmap on Ubuntu and FreeBSD and it works pretty fine.
Some basic 'nmapping' funs from my Kali Linux Box
Look for visible IP in your network - nmap -sP 192.168.1.0/24
Check the number of ports opened - nmap -Ss 192.168.1.0/24
Find the operating systems being used in the same network - nmap -O 192.168.1.0/24
You can even check the ACK bit during the TCP handshake authentication - nmap -sA 192.168.1.0/24
[caption id="attachment_328" align="aligncenter" width="692"]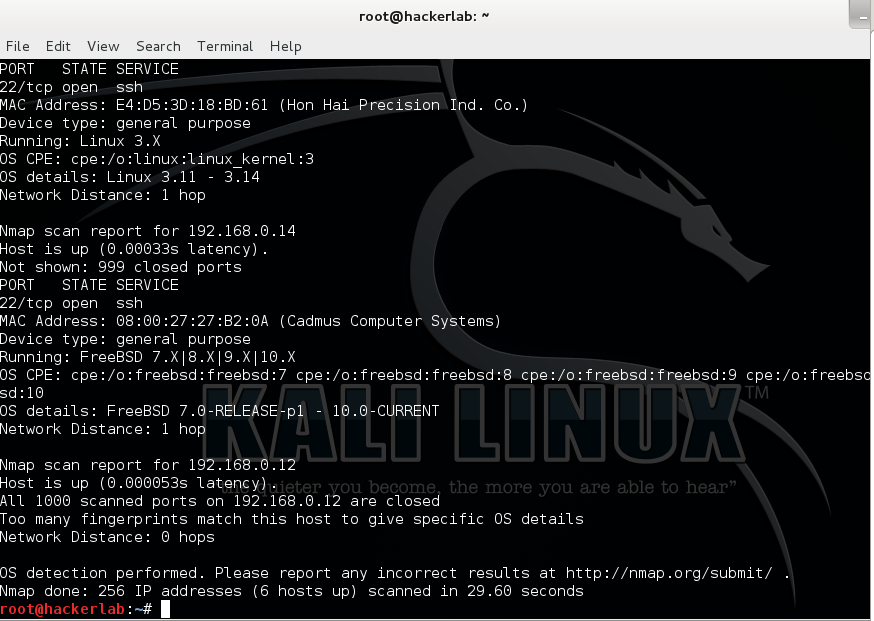
Of course, the world of Nmap is so vast that you will need to go through the Manual to design your own way of exploring the Nmap command. There are many features and capabilities such as Hosts identification, Port scanning, Interrogation of network services, OS detection, etc.. How does Nmap work? Since every hosts or device are connected to a network and has some network ports open and is consequently waiting for connections, the Nmap tool initiate connection to the 1000 most used ports whether it is open responding to an incoming connection, closed and has no service running but can respond to probes, filtered; i.e protected by a Firewall, unfiltered; post can be accessed but no chance to determine if its opened or not and the last one is the open/close filtered.

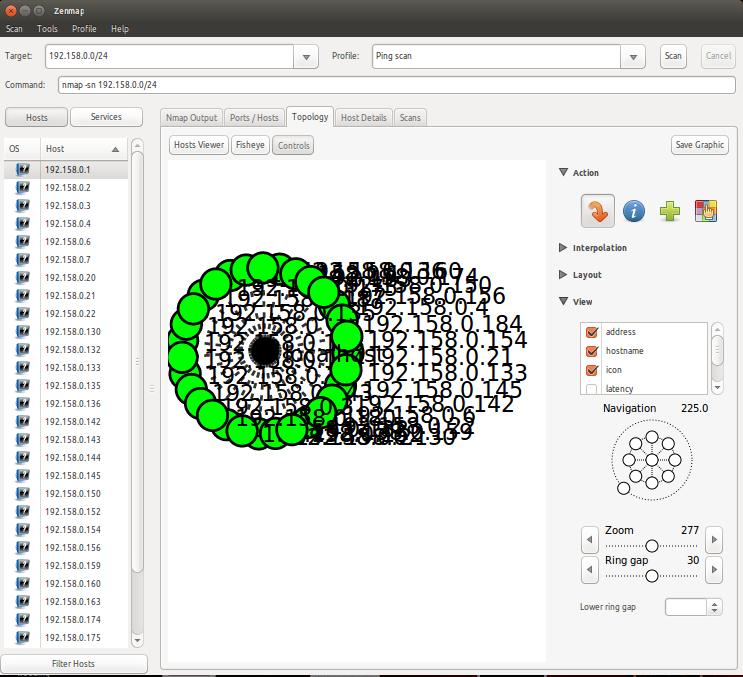
What is more interesting is the ZeNmap tool where you can scan the network using GUI. At this level, parameters are defined as Paranoid, Sneaky, Polite, Normal, Aggressive and Insane.
[caption id="attachment_330" align="aligncenter" width="673"]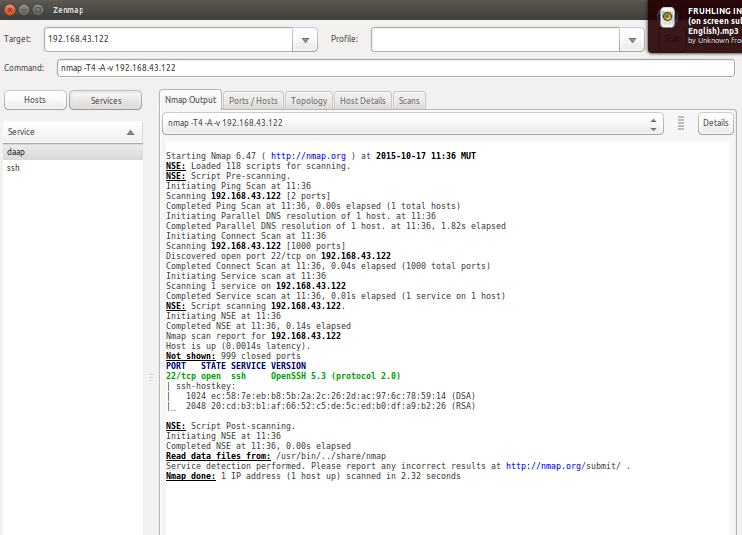
ZeNmap can also be used for firewall evasion techniques, source address and port spoofing, setting flag values on both IP and transport levels. Results are also shown through a Map.