If you think about the number of attacks on the rise in the world, statistics and figures would prove you all. For example, if you think about preventing attacks such as Man-in-the-Middle attacks, guidance in implementing the right TLS Protocol, formerly called SSL is important. TLS is the security protocol that underlies the web. Passive attacks such as tapping – Monitoring of unencrypted communications, Encryption – Intercepting encrypted information flows, Scanning – Scanning ports connected on the Internet and Traffic analysis – building and processing of information from data analysis are surely on the rise. The RFC 7258 as described emphasized on pervasive monitoring mitigations where possible. Pervasive monitoring is also described as an attack and therefore it is an offense.
In 2017, we had so many cybersecurity disasters – Active attacks such as the Shadow Brokers which claimed to have breached the spy tools of the elite NSA-linked operation known as the Equation Group. We had also the WannaCry which netted almost 52 bitcoins, or about $130,000. The Wikileaks CIA Vault 7 which contains alleged spying operations and hacking tools. The cyberstorm.mu team, clearly reacted on this issue under the Operation Crypto Redemption and submitted several patches and encouraged many Open Source organizations to patch up those vulnerabilities. According to Africa News, only South Africa seem to be impacted. It can clearly be seen that the attackers know which country they are aiming during mass phishing.
AFRICA least hit by WANNA CRY – Photo credits Africanews.com
But hey! If you give a thought about it. Did the attackers really aimed in Africa? Why Africa was not really impacted? I highly doubt that there was pervasive monitoring prior to the attack. It may also not be the case due to phishing as it depends on who got trapped with the malware. Still, phishing on large scale can be behind the intelligence of Pervasive monitoring! On the other hand, Checkpoint demonstrated how the risk is high in Africa with a map below displays the risk index globally (green – low risk, red- high-risk risker, white – insufficient data), demonstrating the main risk areas around the world.
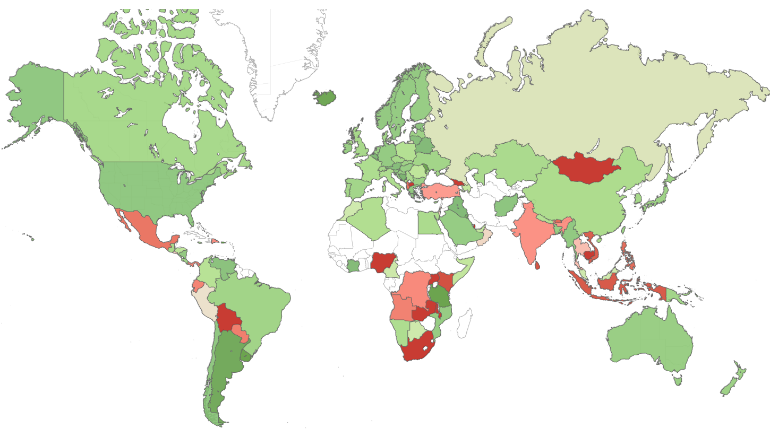
Several countries were listed as white due to insufficient data which could account to reliable data about the risk index in the African continent. Of course, it describes active attacks risks in the African continent. Attacks over countries are now evolving. What I mean is that there could be first a pervasive monitoring system which helps attackers to move further towards their target for example: When to perform mass phishing to get more money!
The fundamental of pervasive monitoring remains mostly about building profiles of a person. It is clear that many are vulnerable to these type of attacks due to the presence on social media and social networks. A nation can be a target! Staffs from a particular company can be a target! But what is most sensible is when the data from pervasive monitoring has already been processed into meaningful information, attackers can sell that information which cost millions and maybe billions of dollars.
Over the past decade, the billion people who live in Africa have experienced the fastest growth the continent has ever seen, and many of its countries (Nigeria, Ethiopia, Mozambique, Guinea) are among the fastest growing in the world. A growing body of evidence backs our view that as Africa’s population doubles to two billion over the next several decades, its GDP will increase from $2 trillion today to $29 trillion in today’s money by 2050. What has changed? Many governments have learned from their mistakes and seen the positive reform examples not just in Asia, but more importantly in Africa itself, from Mauritius to Botswana and Cape Verde, and now Ghana to Rwanda. In most countries there has been no single reform miracle, like China’s in 1978 or India’s in 1991, but rather a series of small steps which taken together have been just as powerful. – cnn.com
Since Africa is on the edge of a rich economy boom, passive attacks will be on the rise probably from many other countries which will want to invest heavily. But where to invest? How much to invest? The information will be on sale probably from a cheap pervasive monitoring instead of an expensive survey!
We all knew that it is difficult to detect pervasive monitoring. However, I believe that data which had been processed from pervasive monitoring can still be analyzed again to understand how it was used. For example, Pervasive data gathered during a previous election campaign comparison with a new election campaign. The dark web is not just being used by individuals. According to Corregedor, private organizations and governments are increasingly using it as a source of threat intelligence. With the threat of cybercrime comes the threat of cyber warfare, and state-sponsored attacks on multinational corporations or other countries. South Africa, as with any other country, is equally at risk from this kind of threat, Corredegor says, because it is difficult to monitor the dark web for national threat intelligence. – mg.co.za
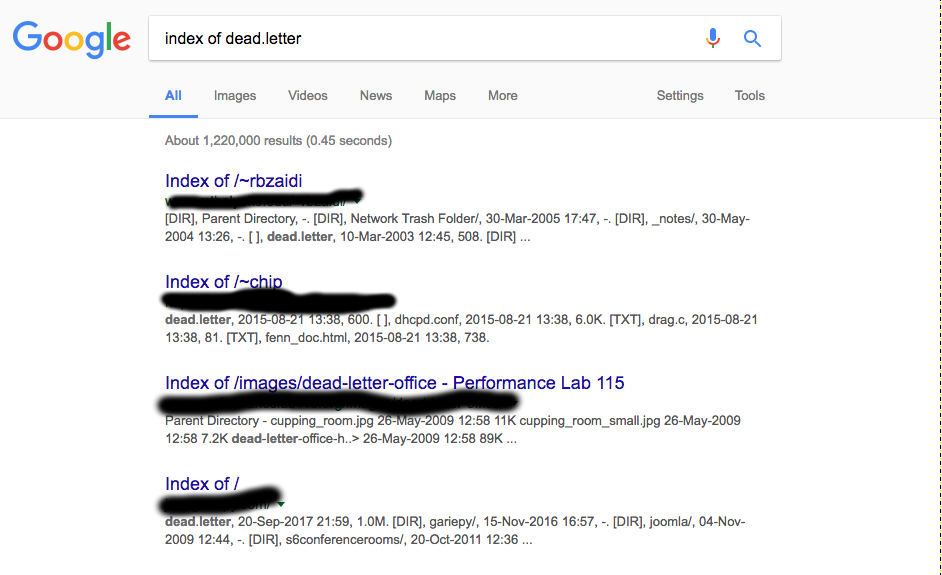
As the first defense, it would be better to adopt TLS to prevent eavesdropping. The use of DNSSEC, SMTP Strict Transport Security and various other security protocols should be taken into consideration. Bear in mind that DNS tells all about you, from where you shop, what you shop online, what web pages you looked out and what you purchased! ISPs should enforce security protocols such as PKIs (Public Key Infrastructure), DANE (DNS Authentication of Named Entities) and DKIM (Domain Keys Infrastructure Mails). Improving internet infrastructure must progress before it is too late. Emails that are not digitally signed are also a good source of data to be processed anew. A simple example of dead.letters can be a source of getting gathering data on the internet.
According to The New York Times, the NSA is monitoring approximately 100,000 computers worldwide with spy software named Quantum. Quantum enables the NSA to conduct surveillance on those computers on the one hand, and can also create a digital highway for launching cyber attacks. A Proof of Concept explained by NetreseC how to detect “Quantum Insert” in the network environment.
One of the various reasons we don’t have much privacy in the online world is that people simply don’t realize the amount of information they leak daily. Worst is when companies leak information on staffs. To resolve such scenarios, since computer today are fast enough, norms to ensure that companies are implementing the use of TCPcrypt can be made mandatory.
REFERENCES:
- https://tools.ietf.org/html/rfc7258
- https://www.wired.com/story/2017-biggest-hacks-so-far
- http://www.africanews.com/2017/05/15/africa-least-hit-by-wannacry-ransomware-cyber-attack/
- https://blog.checkpoint.com/2017/06/20/mays-wanted-malware-fireball-wannacry-impact-1-4-organizations-globally
- http://globalpublicsquare.blogs.cnn.com/2013/01/22/get-ready-for-an-africa-boom [CNN blog retired. I removed this hyperlink in 2023]
- https://mg.co.za/article/2016-07-15-00-beware-of-the-webs-dark-side
- https://www.nytimes.com/2014/01/15/us/nsa-effort-pries-open-computers-not-connected-to-internet.html
- https://www.netresec.com/?page=Blog&month=2015-09&post=Covert-Man-on-the-Side-Attacks