Some days back, i received an invitation to attend an online course by Varonis on Web Security Fundamentals which has been conducted by Troy Hunt. I should say though this course is for beginners, its worth watching and pretty interesting. Troy Hunt is a security developer and author of PluralSight tutorials. You can join the course at Web Security Fundamental on Varonis website.
Some world biggest data breach examples were enumerated at the beginning of the mini course followed by some statistics and the impact of web security. The following points were enumerated:
- SQL Injections
- Insufficient Transport Layer Security
- Insecure Password Storage
- Cross site Scripting (XSS)
- Weak account management
The course composed of the impact of the risk, how it works with examples and demos as well as defense techniques to be used to strengthen the system.
SQL Injection
[caption id="attachment_1418" align="aligncenter" width="762"]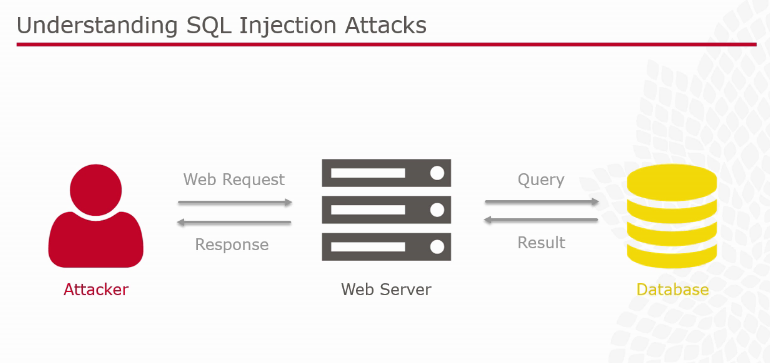
An example given using tool such as Havij to automate SQL injection. This tool is a GUI pretty straight forward such as to enter the URL, followed by the tables, columns etc.. to retrieve information from a database. This will result in leaking of information from a website is same is not secured. Several ways to defend against SQL injection attack is to :
- Validate untrusted data - Has the user provided valid input to the system?
- Parameterize queries - Seperate the query and the data
- Lock down the Database permission - Apply the 'principle of least permission'
- Apply 'Defence in depth' - Web application firewall and cryptographic storage
Transport Layer Security
[caption id="attachment_1420" align="alignnone" width="765"]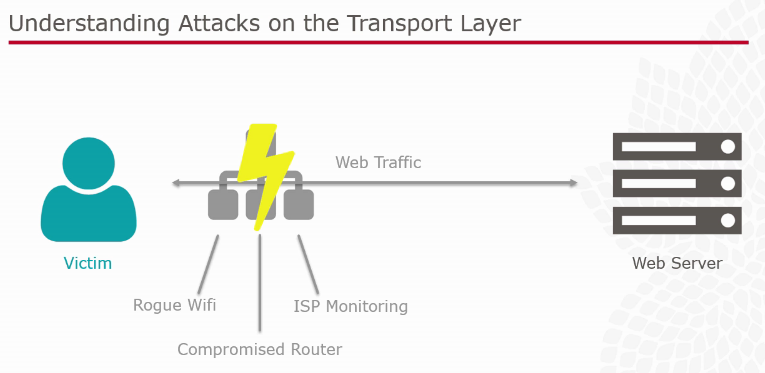
This part was elaborated on the lack of encryption on network layer such as missing HTTPS security, especially how the risk manifest. An example of a key logger was used to retrieve information from a web page. Defense of such type of attacks were emphasized on the following points:
- Apply TLS - Literally apply TLS to encrypt by default
- Strengthen TLS - Ensure it is a strong implementation of TLS
- Lock down Application - Use construct that disallow communication over insecure connections.
- Apply the same control internally - Attacks on the Transport layer can occur behind firewall too
Insecure Password Storage
[caption id="attachment_1421" align="alignnone" width="774"]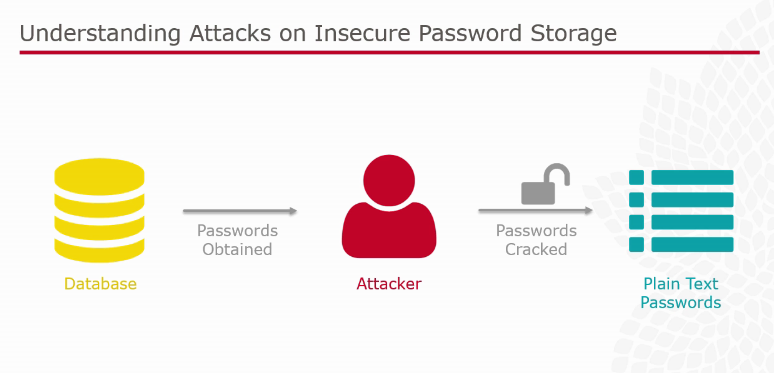
Encryption and Decryption mechanism need to be mastered at this level as this is the basic concept of preventing attacks on insecure password storage. An example of brute force attack was demonstrated. One of the tool is Hashcat which was used as proof of concept. To prevent such types of attacks:
- Always hash and never encrypt - This work on the assumption that the entire system may be compromised.
- Choose the right algorithm - Get the balance between workload and performance right.
- Enforce password rules - Stronger password are significantly harder to crack.
- Encourage strong password - Do not place arbitrary limits on password strength
Cross-Site Scripting (XSS)
A demo was shown on this aspect using a "search" example on a website search engine. The aim is to search mechanism that can be exploited.
[caption id="attachment_1422" align="alignnone" width="770"]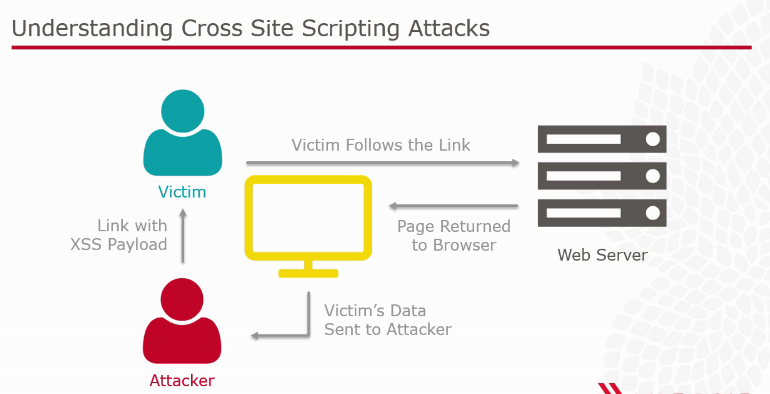
- Defense against such type of attacks were on the following points:
- Validate untrusted data - Has the user provide valid input to the system?
- Always Encore output - Ensure that any reflected input is rendered in the browser
- Encode for the correct context - HTML / HTML attribute / CSS / JavaScript are all different
- Protecting cookies - Flag cookies as 'http only' so they cannot be accessible by client script.
Weak Account Management
[caption id="attachment_1423" align="alignnone" width="769"]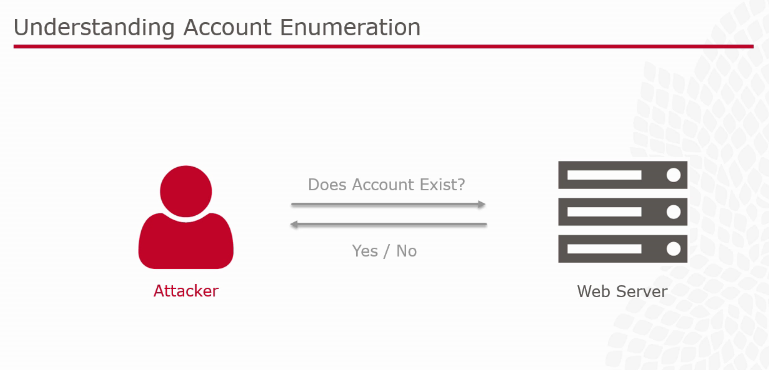
To manage weak accounts, the following factors need to be taken into consideration:
- Poor password rules
- Lack of brute force protection
- Insecure 'remember me' feature
- Vulnerable password change feature
- Enumerable password resets
Here are some tips against account enumeration attacks:
- Always respond identically - Return the same message to anonymous users
- Use email for verification - Email the address and confirm or deny account existence there
- Consider other enumeration vectors - Login and registration are other common channels for disclosure.
- Consider the risk in context - Different application have different levels of privacy expectation.
To resume, its important to grasp the fact that good security is 'defense in depth'. Security needs to be considered in the context of cost as well as usability as many of these attacks provide vectors into the internal network. Security goes well beyond. The tutorial ensures that questions are being asked at all levels to ensure security such as:
- Is access to data logged and auditable?
- Do you have visibility to resource accessible via access controls?
- How many of these permissions excessive?
- Is anyone actually reviewing entitlements?
- How are you prioritizing security efforts?
